Pimeyes face search alternative:Is there a site better than PimEyes?
Looking for a PimEyes face search alternative? This page lists reliable options and explains which tools work better for privacy, social media image checks, and misuse detection.
Removing leaked private photos fails most often not because people act too slowly, but because they act without full visibility.
In repeated leak cases, the first takedown is rarely the last. What looks like a single post is often only the first visible instance of a wider spread. Effective removal depends on confirming scope before attempting cleanup.
This article explains how to remove leaked private photos in a way that actually reduces repeat exposure.
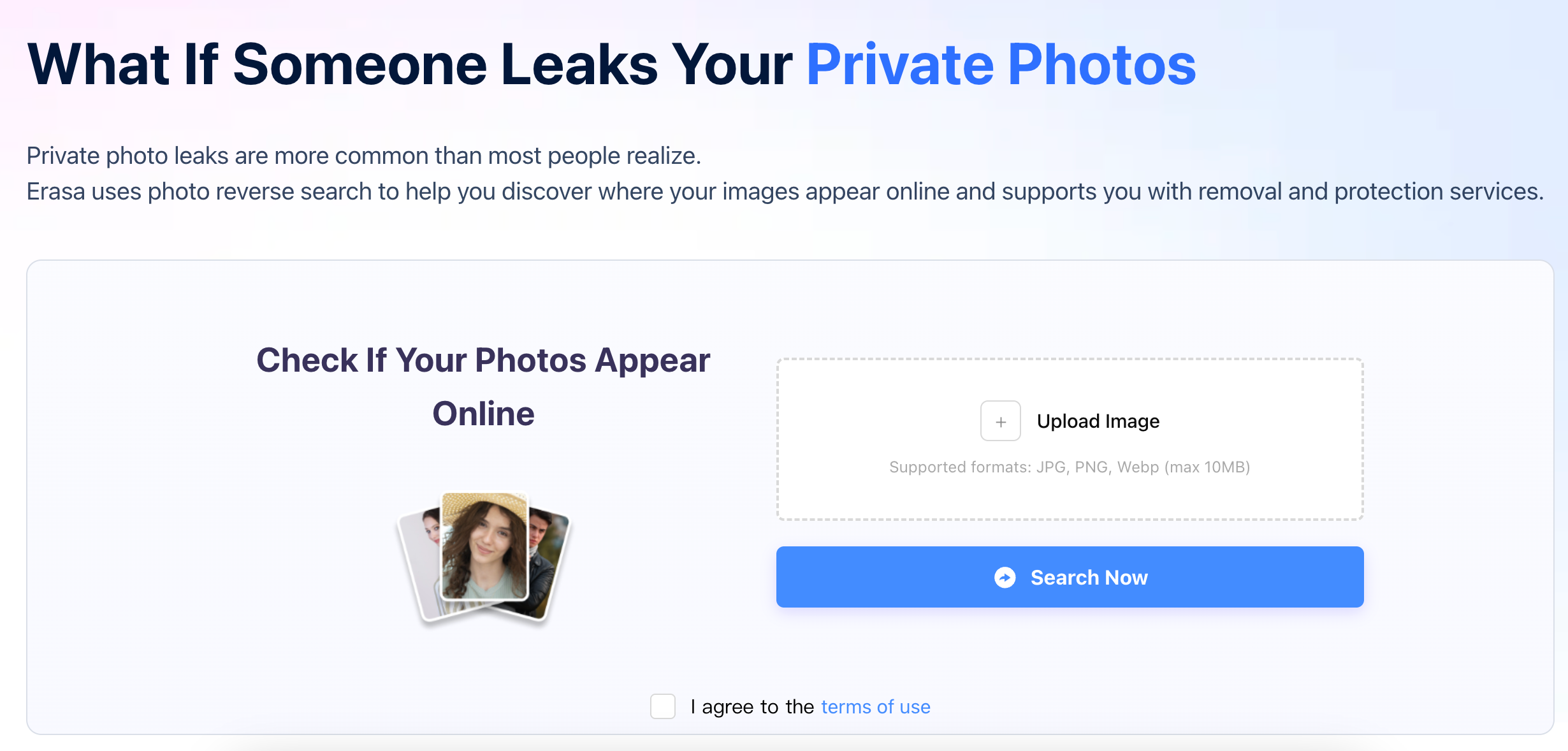
Before any removal attempt, you need to confirm where your private photos are already appearing online.
Across repeated leak scenarios, one pattern appears consistently: reposts are usually discovered after the original link is removed. Copies surface under different usernames, on secondary sites, or inside smaller communities that were never checked in the first place.
When people try to remove leaked private photos based only on the first link they see, missed copies are inevitable. Manual searching does not scale once images are resized, cropped, or stripped of context.
At this stage, confirmation is not optional. You need to determine whether the incident is isolated or already distributed across multiple locations.
Photo-based detection tools make this possible. By uploading an image, you can confirm whether your private photos appear online and identify where reposts or impersonation accounts exist. This step does not remove content; it establishes reality.
If you need to find where leaked private photos appear before proceeding, the detection process is outlined on the leaked private photos page.
Once a leak is confirmed, sequence matters.
In most cases where follow-up actions fail, evidence was lost too early. URLs, usernames, timestamps, and screenshots should be preserved before any takedown request is submitted.
Account security comes next. A significant portion of leaks originate from compromised access rather than intentional sharing. Changing passwords for email, cloud storage, and social platforms, enabling two-factor authentication, and removing unknown devices prevents further exposure during removal.
Removing leaked private photos is rarely a single-step process.
Platform reporting is necessary, but it only works for locations you already know. In multi-site leaks, this creates blind spots.
Search engine removal requests reduce visibility but do not remove original files. In repeated cases, reposts typically appear after delisting succeeds, not before.
Manual reporting works for isolated posts. Once leaks span more than one platform, this approach stops scaling. At that point, the limitation is not effort, but coverage.
Most people consider tools like Erasa only after initial removal attempts stop reducing exposure.
This stage is typically reached when:
At this point, the challenge is no longer how to file reports, but how to maintain visibility as the image continues to move.
Erasa is designed around this reality. It prioritizes detection so removal actions are based on confirmed matches rather than guesswork. This reflects how repeated leaks behave in practice, where awareness matters more than speed.
Many users begin with a free check to determine whether the leak is contained or already wider than expected. The detection and removal workflow is detailed on the What If Someone Leaks Your Private Photos page.
Across repeated cases, prevention failures tend to follow the same patterns.
Risk is reduced by limiting access points rather than reacting to individual incidents. Unique passwords, two-factor authentication, controlled storage of sensitive images, and periodic checks for reposts reduce repeat exposure over time.
Prevention works best when paired with ongoing awareness, not one-time cleanup.
Removing leaked private photos succeeds only when confirmation comes first.
In most repeat cases, failure occurs because the scope of the leak was underestimated. Effective response follows a clear order: confirm where the photos appear, remove known copies, and watch for reposts.
Without visibility, removal becomes reactive and incomplete. Start by confirming the full scope, then act.
How do I know if my private photos were leaked?
Photo-based detection tools can confirm whether your images appear elsewhere online, even if you have only seen one instance.
Can leaked private photos be fully removed?
Complete removal depends on how widely the photos were shared, but repeated exposure can often be significantly reduced.
Why do leaked private photos keep reappearing?
In most cases, images are copied before the first takedown is completed, leading to reposts later.
What should I do first after discovering a leak?
Preserve evidence, secure your accounts, and confirm where the photos are posted before attempting removal.
Looking for a PimEyes face search alternative? This page lists reliable options and explains which tools work better for privacy, social media image checks, and misuse detection.
Looking for PimEyes alternatives? Compare safer reverse face search options, understand privacy concerns, and find tools better suited for tracking fake profiles or reused photos.
Learn how to check if your video has been leaked, where stolen videos usually spread, and what to do if your content is reposted without permission.
Reverse image search can’t identify faces. Learn why it fails, how face-search tools work, and how to find where your photos or identity appear online.
Learn why your Twitter (X) reach suddenly dropped. This guide explains the real reasons behind shadowbans and how to confirm your visibility status in minutes.
Compare the best feet pics platforms for 2025. Learn how to sell safely, stay anonymous, avoid scams, and protect your content with Erasa.